Table of contents
1. Routing
We consider the following network and its routing tables.
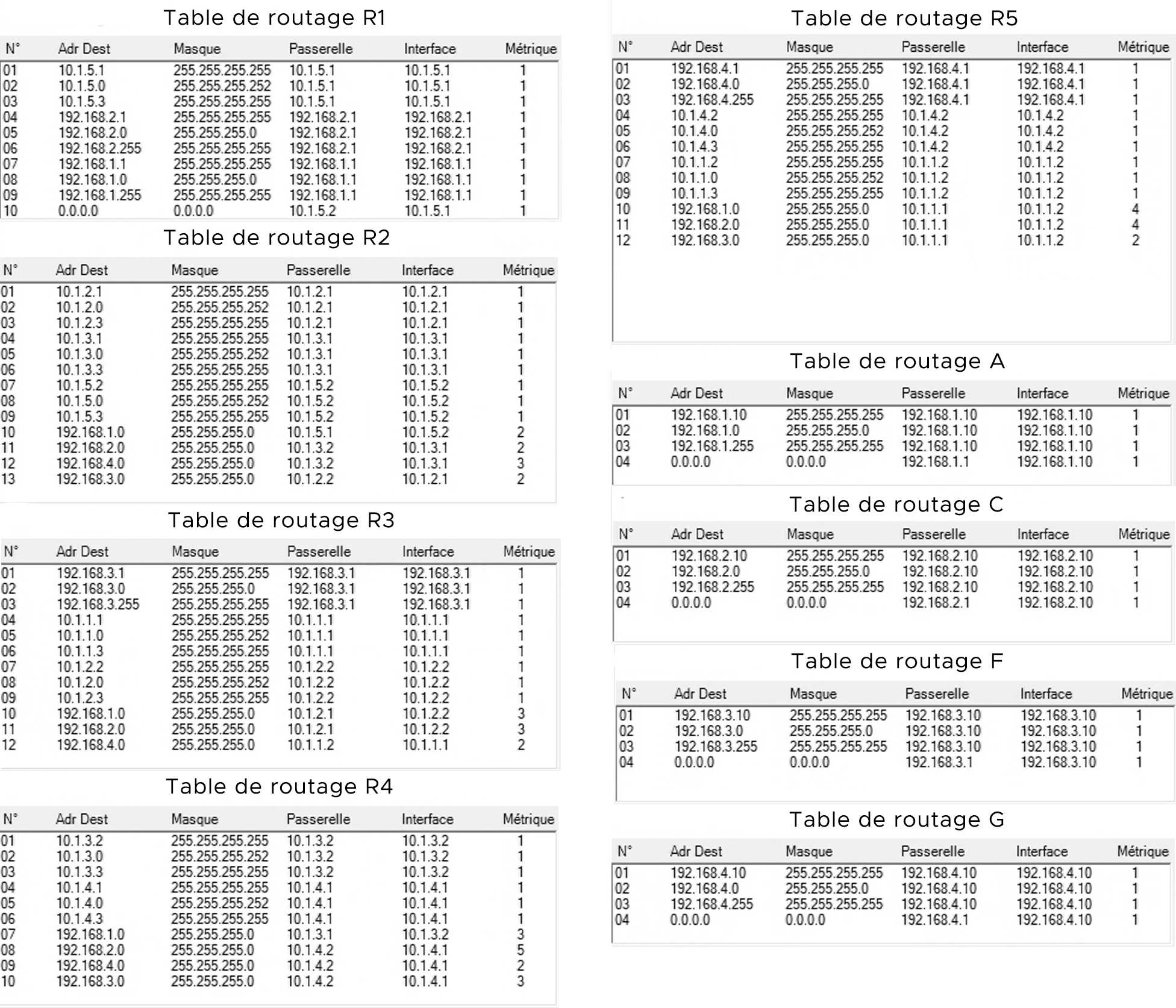
What are the round-trip paths followed by the packets of a ping from A to G?
ANSWER ELEMENTS
from A to G: A, R1, R2, R4, R5, G. from G to A: G, R5, R3, R2, R1, A.
The two paths are not the same, but this doesn't pose any problem and is common in computer networks.
What are the round-trip paths followed by the packets of a ping from G to C?
ANSWER ELEMENTS
The packets loop in the network without reaching the destination. IP packets are associated with a TTL (time-to-live), a counter that is decremented each time a packet goes through a router. When the TTL reaches 0, the packet is dropped. This prevents looping packets from clogging the network.
Where is the configuration error? How do you solve it?
ANSWER ELEMENTS
We need to correct one of the routing tables. For example the route to 192.168.2.0 on router R2.
2. Ethernet and IP
We are interested in the following network configuration. A home network is connected to the Internet using the residential gateway of an Internet provider.
The local computer, with the address 192.168.0.2 sends a message to a computer with the following address : 8.1.3.8. Which protocols are used in the local network?
ANSWER ELEMENTS
The home network uses the Ethernet protocol for layers 1 and 2 (physical and link) and IP for the layer 3. We did not specify the application associated with the message, thus we cannot give more information, in particular the port and the transport layer protocol (TCP or UDP).
Describe a typical frame sent by the local computer to the residential gateway. In particular, describe its structure and the main information in the Ethernet and IP header.
ANSWER ELEMENTS
The frame is the following:
| Eth src. | Eth dest. | IP src. | IP dest. | Data |
6E:...:03 | 56:...:13 | 192.168.0.2 | 8.1.3.8 | ... |
Suppose now that 8.1.3.8 is a web server. The local computer sends a request to get the page "index.html". What are the involved protocols? Complete the frame given in the previous exercise.
ANSWER ELEMENTS
The involved protocols are TCP and Hypertext Transfer Protocol (HTTP). The HTTP request "GET index.html" is encapsulated into the TCP protocol.
A TCP message is sent to a destination port, which is 80 for HTTP. There is also a source port which will be used by the web server to send its response.
| Eth src. | Eth dest. | IP src. | IP dest. | TCP Port src. | TCP Port dest. | HTTP |
6E:...:03 | 56:...:13 | 192.168.0.2 | 8.1.3.8 | 50001 | 80 | GET index.html |
The frame that you previously described reaches the gateway. The gateway modifies it before forwarding over the Internet. What are the modifications?
ANSWER ELEMENTS
The source IP address is changed because the addresses 192.168/32 are private. The new source IP is the external address of the gateway: 87.52.7.5.
The Ethernet protocol header is removed from the frame as it is only supported on the local Ethernet network.
We do not know the protocol used on the network linking the gateway and its provider network. Depending on the nature of the residential gateway (optical fiber or DSL), it is likely that the protocol carrying IP is FTTH (Fiber to the home) or VDSL2. Without this information, we cannot fully describe the frame.
| FTTH or VDSL2 Header | IP src. | IP dest. | TCP Port src. | TCP Port dest. | HTTP |
| ... | 87.52.7.5 | 8.1.3.8 | 50001 | 80 | GET index.html |
The server receives the GET request, then sends back the HTML code of the web page. Describe the frame.
ANSWER ELEMENTS
The destination IP is the external IP of the gateway. The destination port is the port which was previously the source port.
The data carried by the frame is the source code of the web page.
As we don't have any specification on the network which the server is connected to, we cannot specify the Ethernet header.
| Ethernet Header | IP src. | IP dest. | TCP Port src. | TCP Port dest. | HTTP |
| ... | 8.1.3.8 | 87.52.7.5 | 80 | 50001 | <HTML><HEADER>...</BODY></HTML> |
When the response reaches the gateway, it is forwarded to the destination computer. What modification to the response are made by the gateway?
ANSWER ELEMENTS
The destination IP is replaced with the IP of the destination computer.
As the local network uses Ethernet, the IP frame is encapsulated into an Ethernet frame.
| Eth src. | Eth dest. | IP src. | IP dest. | TCP Port src. | TCP Port dest. | HTTP |
56:...:13 | 6E:...:03 | 8.1.3.8 | 192.168.0.2 | 80 | 50001 | <HTML><HEADER>...</BODY></HTML> |
3. Internet from our perspective
The ifconfig command (on macOS), or ipconfig (on Windows, using PowerShell as terminal), that you can type in a terminal returns the network interfaces available on your machine. You might have several. Interfaces denoted loX (where X is an integer) correspond to the so-called loopback interfaces, in particular the 127.0.0.1.
You should also have enX (on OSX) or ethX (on Windows) interfaces for ethernet interfaces. This can correspond to wired or wifi interfaces.
Identify the primary IP address of your machine. You can find this information in the system preferences.
ANSWER ELEMENTS
Open the system preferences of your operating system and select the network configuration.
The ping command allows you to send a request to a server to find out if it is online.
The command also returns the "round-trip time" (RTT), that is the time that a message takes to travel from your machine to the server, and the response to travel back to your machine.
Some servers may not respond to ping requests for security reasons.
Ping the following servers, what conclusions can you draw about the RTT?
paris-saclay.frwww.mcgill.caweb.aiu.ac.jp
ANSWER ELEMENTS
The RTT increases with the distance to the server. However, the RTT is very long compared with the speed of signal propagation. A RTT of 200ms to reach for the university in Tokyo seems long, considered that at the speed of light the signal can travel back and forth in 8ms. The reason is that IP packets go through several routers, each router processes a lot of packets and they need some time to do so. Hence, a packet may be kept for some time in the buffers of some routers.
Update 2024 : the ping on web.aiu.ac.jp is indeed done on a content delivery network provided by Amazon (CloudFront), so the RTT is only some ms. You can try to ping www.u-toyama.ac.jp which is not using such a system.
Repeat the same experiment with the following servers. What can we conclude?
google.frgoogle.cagoogle.jp
ANSWER ELEMENTS
The RTT is more or less the same. If we look at the IP addresses in the ping response, we realize that they always refer to servers based in the US.
Update 2024 : there is no way to know for sure the exact location of machine having a given IP address. Try iplocation to see different results.
The traceroute command (on macOS), or tracert (on Windows, using PowersShell as terminal), allows you to determine the routes followed by a ping request to reach a remote server.
Some intermediate servers may not respond. Test the command on the following servers:
paris-saclay.frwww.mcgill.caweb.aiu.ac.jp
Then for the following destinations.
google.frgoogle.cagoogle.jp
ANSWER ELEMENTS
For the universities, we should see a path through the CentraleSupélec network, RENATER, and, possibly, GEANT. Note that for a certain number of hops, you can get several IP addresses. The reason is that Traceroute sends several packets, and some might follow different paths. As for the Google addresses, we see that the packets always reach proximate locations, they certainly don't reach Japan nor Canada.
4. NAT -- Network address translation
We suppose now that the networks are a little more complex.
Why is it possible for two computers to share the same IP address: 192.168.0.2?
ANSWER ELEMENTS
This IP is local. All messages sent by local computers to the outside world are modified by the gateway. The gateway replaces the source IP with its external IP. That way, when the web server sends a response, it uses either 87.52.7.5 or 92.5.2.1 as the destination IP address.
In the home network 1, we have different computers. Any of them can send a message to the server. With the previous strategy (replacing the local IP by the external IP of the gateway), there is a problem when the gateway receives a response from the server. The gateway doesn't know to which local computer the message is supposed to be forwarded.
Can we imagine a solution deployed on the residential gateway using the notion of ports to solve this problem?
ANSWER ELEMENTS
- NAT is not part of the course.
- Only replacing the private IP address with the public address of the residential gateway does not work.
If several computers send frames to the outside world, the router needs to keep track of which computer sent which frame.
- The solution of NAT is to use port numbers (see the following schema).
5. Services (Firewall, proxy, DNS)
What is a firewall? In which points of our network can we find firewalls? How are they configured?
ANSWER ELEMENTS
- A firewall is a device that controls the flow of data and filters incoming and outgoing traffic. A firewall can isolate parts of the network.
In general, there are at least two areas: Internet, where one should adopt a no trust policy, and an internal network.
- Data is filtered according to the following criteria:
- the origin or destination of the packets;
- type of protocols (TCP / UDP);
- the data itself (size, match to a pattern, etc.);
- users (for the most recent firewalls).
- A firewall is often associated with a router or even a NAT (the residential gateway contains a firewall which protects the computers of the network).
- Typically we find a firewall at the residential gateway. They are configured to allow all outgoing traffic to pass but cut off all incoming traffic, whatever the port, except that recorded in the NAT table. Packets that form the response of a request initiated by the computers in the local network are allowed.
- There is also a firewall at the router level of the web server farm. It allows incoming TCP messages to pass on port 80 (HTTP protocol) and TCP on port 443 (HTTPS).
What is a proxy? Why is it used in combination with a firewall?
ANSWER ELEMENTS
- A proxy is a network device that aggregates the HTTP/HTTPS requests of several users. The goal is to save traffic by pooling requests using a cache, and filter requests to restrict accessible websites.
- The web client (e.g., the browser) of each user has to be configured to use a proxy. To force users to do so, and prevent them to have a direct access to websites, ports 80 and 443 are blocked on the local network (except for the proxy).
What is DNS (Domain Name System)? Describe the protocols that are used with DNS.
ANSWER ELEMENTS
- DNS uses UDP as a transport layer protocol. In fact, DNS consists of many short requests, in which case TCP is not a good choice.
- For a description of how it works, you can refer to the corresponding Wikipedia page.
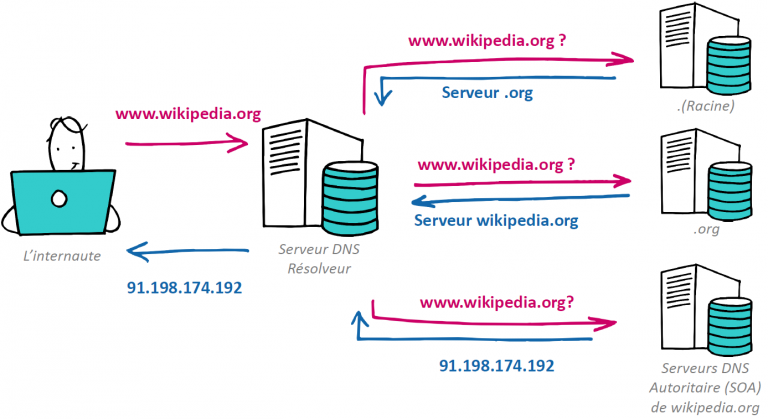
Modify the diagram of this exercise to show the different components that we have just seen (NAT, firewall, proxy and DNS).
What is the sequence of messages that are necessary for a Web browser to get the page
http://www.example.fr/index.html stored at the server with IP address 8.1.3.8?
ANSWER ELEMENTS
1. The browser extracts the hostname, www.example.fr, from the URL and sends it to a local DNS server L (the one managed by the internet provider).
2. The DNS server L sends the hostname to a root DNS server R.
3. R returns to L a list of IP addresses of top-level DNS servers for the domain .fr
4. L sends the hostname to one of these top-level DNS servers.
5. The to-level domain returns to L the IP address of the DNS server that is authoritative for the domain example.fr.
6. L sends the hostname to the authoritative DNS server.
7. The authoritative DNS server returns to L the IP address corresponding to the requested hostname.
8. L sends to the web browser the requested IP address.
9. The web browser sends an HTTP request to the received IP address to get the page index.html. HTTP requests are encapsulated into TCP segments. A simple HTTP request require several TCP segments.
10. The server sends the requested page to the Web browser.
Note: The authoritative DNS server stores the IP-hostname mappings that are retrieved via the DNS protocol. It is called "authoritative" because, by definition, what it says is the truth. It is never queried directly by the users' machines, but through the other DNS servers, also called the resolvers.
6. Wireshark
Demonstration of Ping, Traceroute and Wireshark. Observe the frames, the encapsulation, the order of the requests and especially the TCP session and the acknowledgment of messages.
If your teacher does not have the time for this demonstration, this video (in french...) explain everything. Wireshark.mp4
ANSWER ELEMENTS
- Few slides to show what can be done with ping et traceroute : demo_ping_traceroute.pdf
- Une trace simple à utiliser avec Wireshark : sciencespo.pcapng
- Une vidéo expliquant tout ce qu'on peut dire à partir de la trace : Wireshark.mp4

